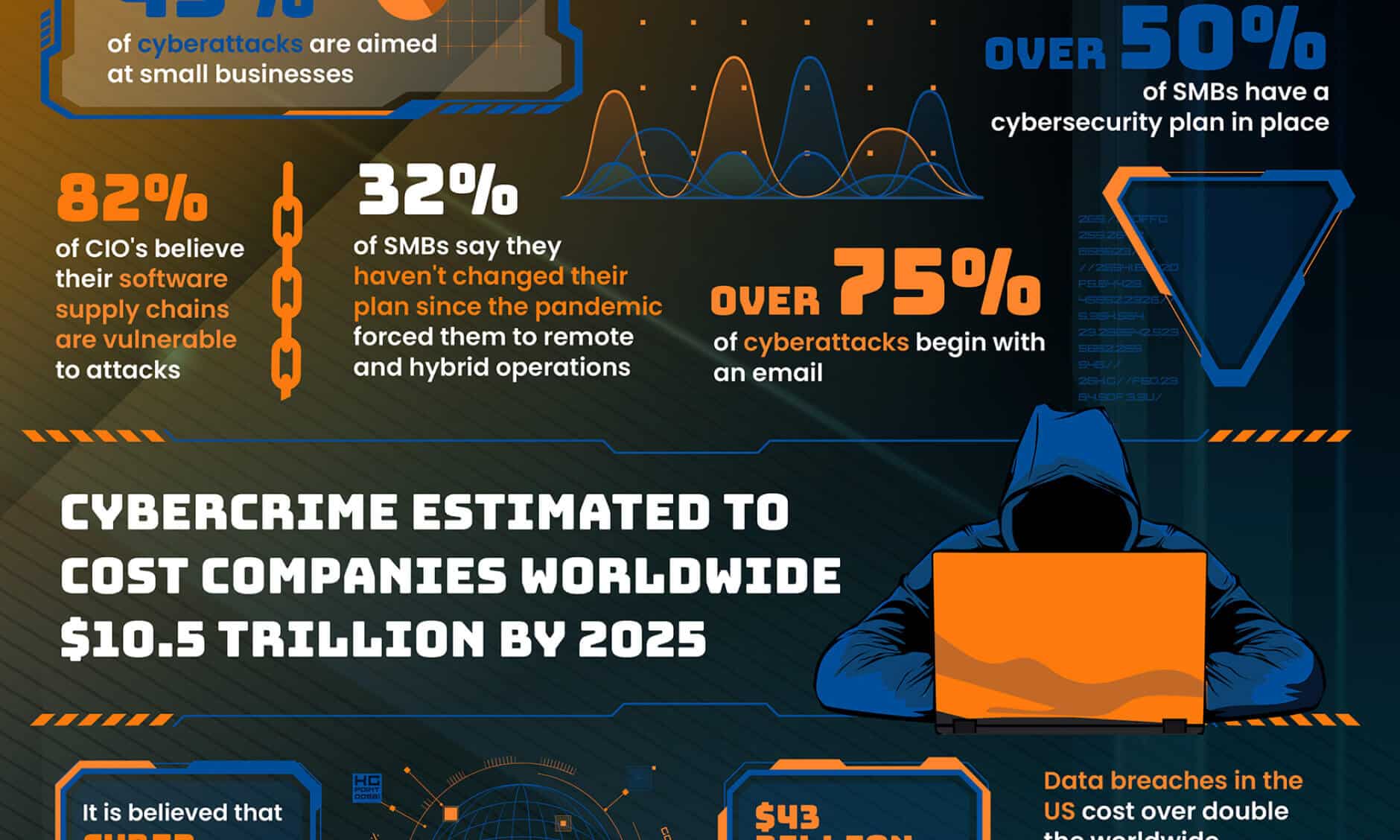
For businesses going through digital transformation, managing the increased volume and complexity of data — coupled with the risk of cyber threats and human error — can quickly become an additional overhead that serves only to burden your operations team.
Enter data loss prevention (DLP). DLP software plays a crucial role in safeguarding businesses from both internal and external threats by monitoring, detecting, and blocking data while in use, in motion, and at rest.
Understanding data loss prevention (DLP)
Data Loss Prevention (DLP) is a strategy that prevents sensitive or critical information from leaking outside of a corporate network.
With DLP, engineering and operations teams can enforce data security policies, ensure regulatory compliance, and provide visibility into data movement, leading to enhanced overall data security and integrity.
Organizations can implement DLP through software that monitors and controls endpoint activities, filters data streams on corporate networks, and monitors data in the cloud to protect data at rest, in motion, and in use.
DLP software identifies confidential data, tracks that data as it moves through and out of the enterprise, and prevents unauthorized disclosure of data by creating and enforcing disclosure policies. These policies define critical data and outline the controls to enforce, such as alerting, encrypting, and other protective actions.
Data loss prevention tools come in all shapes and sizes. Some of them are focused on things like endpoint security and email protection, while others take on advanced network safety using tools like IP geolocation and VPN detection. The specific type of DLP software your company needs will depend on the nature and size of your business, as well as the setup of your network architecture.
Types of data loss prevention software
Each type of DLP software plays a unique role in a comprehensive data protection strategy, which is why many organizations use a combination of different types to cover all their bases against expensive cybercrime:
- Network DLP: These solutions are typically installed at the network perimeter, such as at the exit point of a corporate network, and are used to monitor and control data in motion. They analyze network traffic to detect valuable data sent in violation of information security policies.
- Storage DLP: Also known as Data at Rest DLP, these solutions identify and secure data stored in data centers, cloud storage, file servers, databases, and other storage devices. They ensure that stored data is kept safe from unauthorized access and breaches.
- Endpoint DLP: Organizations install these solutions on end-user devices such as computers, laptops, and mobile devices. Endpoint DLPs control data in use and monitor transferred data. They can also control data uploads and prevent malicious activities.
- Cloud DLP: Designed to protect data stored or shared in the cloud, organizations can integrate these solutions with cloud-based services to monitor and control data access and movement, ensuring compliance with regulations like HIPAA and GDPR.
- Email DLP: These solutions monitor and control data sent via email. Organizations use email DLP to prevent sensitive information from being shared with unauthorized individuals, both within and outside the organization.
- Content-aware DLP: These solutions are capable of inspecting and contextualizing the content being sent or accessed. They can identify data based on pre-defined policies and take action to prevent unauthorized sharing.
How to choose the right data loss prevention software
Choosing the right data loss prevention (DLP) software is a critical decision that can significantly impact the security of your organization’s data. Here are some factors to consider when choosing the right DLP tool:
- Data architecture: Once you know what data you need to protect, you can look for a DLP solution that offers features tailored to protect that data. For instance, Safetica offers templated data classification, which can be useful if you have specific types of data you need to protect.
- Coverage: The DLP solution should cover all potential data leakage points, including email, web, cloud services, network, and endpoint. For example, Forcepoint DLP offers unified data protection coverage across all these channels.
- Ease of use: The DLP solution should be user-friendly and not require extensive technical expertise to operate. It should offer intuitive interfaces and easy-to-understand reports. ManageEngine Endpoint DLP Plus, for instance, is designed for user dexterity and precision, making it easy to configure and deploy policies.
- Policy management: The ability to create, manage, and enforce policies is a crucial feature of a DLP solution. The software should allow you to easily tailor policies to match your organization’s needs. For example, NinjaOne Backup offers automated backup policies users can customize based on their requirements.
- Integration: The DLP solution should integrate well with other security and IT systems in your organization. This can help streamline your security operations and provide a more holistic view of your security posture.
- Scalability: The DLP solution should be able to scale as your organization grows. It should be able to handle an increasing amount of data and a number of users without performance issues.
- Vendor reputation: Consider the reputation of the DLP solution’s vendor. Look at reviews and testimonials from other customers, and consider the vendor’s history and experience in the field. Also, consider the level of support the vendor provides. Do they offer 24/7 support? What are their response times like? Can they provide references?
- Pricing: Finally, consider the cost of the DLP solution. This includes not only the upfront cost but also any ongoing costs for maintenance, support, and updates. Keep in mind the most expensive solution is not always the best one for your needs. DLP solutions don’t usually provide pricing information on their websites, so you would need to contact them directly for a quote.
Digital Element: Your trusted intelligence solution for data loss prevention
Choosing the right data loss prevention solution is crucial for safeguarding your organization’s data. Factors such as data architecture, coverage, ease of use, policy management, integration, scalability, vendor reputation, and pricing play a critical role in this decision.
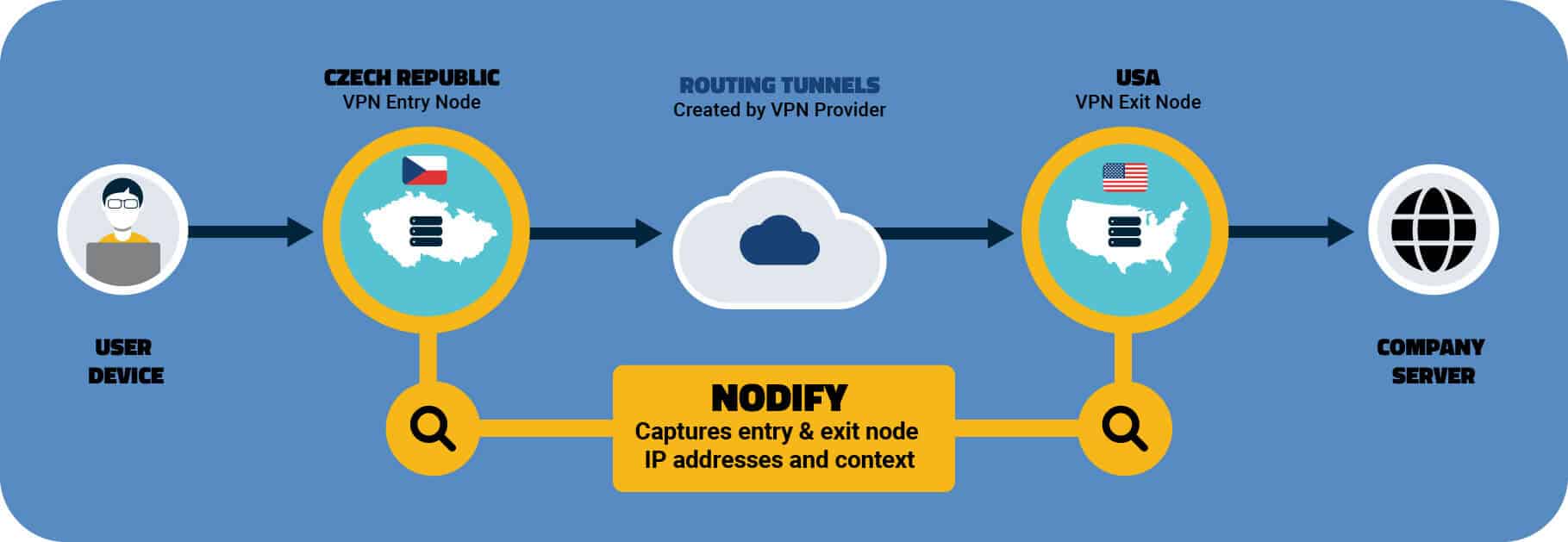
While there are several robust DLP solutions on the market, Digital Element has a unique approach to data protection and is one of the few that uses IP geolocation to safeguard against data loss.
Digital Element is a leading provider of IP Intelligence and geolocation solutions. Our NetAcuity platform provides the most detailed, hyperlocal dataset available worldwide today that complies with the highest standards of end-user privacy.
Key features:
- Hyperlocal IP geolocation: Provides detailed and accurate geographic information.
- Proxy data: Identifies the use of different types of proxy servers to ensure data integrity.
- Mobile carrier identification: Identifies mobile carrier data for better mobile targeting and prevention of fraud.
Looking for a cybersecurity solution? Try Digital Element today
Need help isolating specific malicious actors by location or discovering the source of a data breach? Enhance your cybersecurity strategy today with Digital Element.