According to IBM, the average cost of a single data breach in 2023 is a jaw-dropping $4.45 million. This marks a 15% increase over the past three years.
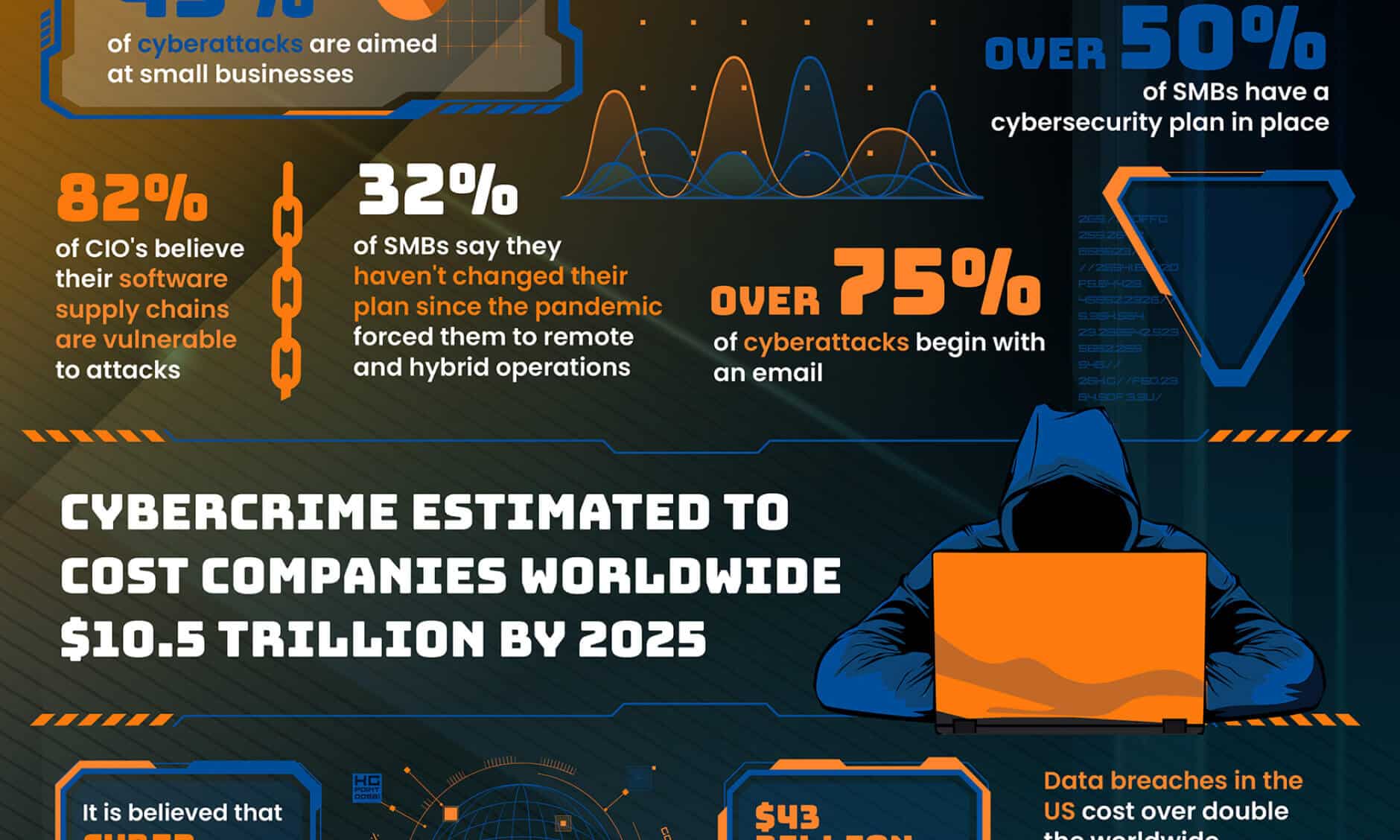
Faced with an ever-growing number of threat actors and security risks, companies need effective security measures and a comprehensive security plan more than at any point in the past.
In this step-by-step guide to building a strategic plan for data protection, we’ll cover everything you need to know to create a cybersecurity framework for your company.
Understanding information security
Information security is the process of securing digital data by mitigating cyber risks.
Given the current state of cyber threats and the importance of risk management, Information security is an essential part of any company’s overall business strategy.
Hackers pose a wide variety of information security threats — from ransomware to phishing attacks to malware. Because of this, there are also a variety of strategies companies use to make their information security program robust and effective.
IP-based data gathering is one of the most important of these strategies.
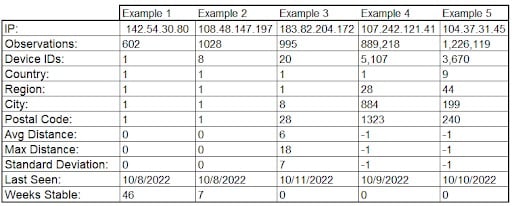
With IP-based data like Digital Element provides, companies analyze the source of their web traffic to see where attacks originate in real time. The data, when used with other security tools, can help identify nefarious traffic before a security incident occurs.
The benefits of an IP-based information security strategy
Companies hoping to strengthen their security posture using an IP-based information security strategy reap many benefits. Some of the benefits of using an IP intelligence data solution like Digital Element to fuel your information security strategy include:
Protects valuable information
The most obvious benefit of an effective IP-based information security strategy (and arguably the most important) is it helps eliminate vulnerabilities to your company’s sensitive data, whether that’s confidential intellectual property, credit card data, or anything else you want to keep private.
Exposing your company’s valuable and sensitive data to bad actors can happen in a single security issue, but IP-based data solutions can help boost network security and prevent this exposure in real time.
IP-based cybersecurity strategies allow security teams to perform traffic and threat analytics that pinpoint where cyberattacks originate and what nefarious traffic looks like. You can then use these insights to set rules and alerts for traffic that meets specific criteria, helping prevent security breaches that could expose your confidential information.
Ensures compliance with regulations
Maintaining a strong security posture isn’t always optional. In many cases, the law requires companies to meet certain IT security standards.
Regulatory requirements and industry standards regarding cybersecurity vary from one industry to the other. For example, the law requires healthcare companies that handle sensitive medical information to comply with HIPAA’s data security requirements. Similarly, the law requires companies handling financial information to comply with the Payment Card Industry Data Security Standard (PCI DSS).
In such cases where strong security controls are a regulatory requirement, adopting an information security strategy helps ensure your company remains compliant and avoids costly fees.
Prevents financial losses
Financial losses due to cyberattacks come in several different forms. From ransomware payments to operational disruption, regulatory fines, or a loss of customers due to reputational damage, there is no shortage of ways porous information security can hurt a company’s bottom line.
By preventing these attacks from occurring (and reducing their impact in the event they are not prevented), IP-based information security can mitigate the financial losses caused by cyberattacks, ensuring a simple vulnerability doesn’t cost your company a fortune.
Improves decision making
A good information security strategy will serve as a roadmap for your company and its IT teams, providing the guidance you need for swift and effective decision-making in the face of a cyber threat.
This allows companies to quickly respond to threats in an organized, collaborative, and appropriate way. At a time when every minute matters, the speed of action an information security strategy enables is invaluable.
Key elements of an effective information security strategy
We’ve mentioned there are a lot of different elements that make up an information security strategy. The exact details of an information security plan will vary from company to company, but the core elements tend to remain the same.
Some of the most important elements to cover in your information security strategy include:
1. Risk assessment
Before you can safeguard against cyber threats, you need to form a complete understanding of the exact threats your company faces. A risk assessment sheds light on these threats as well as your company’s security vulnerabilities.
Risk assessments allow you to identify the threats and vulnerabilities that pose the biggest risk so you can focus on mitigating them. In this way, your risk assessment will guide the rest of your information security strategy, dictating specific security measures you should take and how you can best allocate your company’s cybersecurity resources.
2. Security policies and procedures
Well-defined security policies and procedures establish the framework for how a company handles its data and technology. These documents outline the rules and procedures employees should follow to maintain strong security, covering concerns such as access control, password management, and the acceptable use of company devices.
84% of US-based organizations have stated that conducting regular security awareness training has reduced the rate at which employees fall prey to phishing attacks, so having these policies and procedures in place is vital to maintaining an effective information security strategy.
3. Employee training
Along with providing security policies and procedures to your employees, it’s also important to thoroughly train them on those policies and procedures. By conducting regular training sessions to familiarize your employees with proper cybersecurity practices, you can reduce the risk posed by human error.
Likewise, it’s also important to train your employees on how to respond in the event of a security incident so everyone understands their roles and responsibilities. This will be integral when responding to and recovering from security incidents.
4. Use of secure technology
Implementing the right cybersecurity technology is a pillar of a strong cybersecurity program. Technologies such as antivirus software, firewalls, instruction detection systems, access control/authentication systems, and numerous others all play a vital role in preventing hackers from gaining access to your company’s data.
Choosing and installing the right tools for the job is something every information security strategy should address.
5. Regular audits and updates
Cybersecurity is still a rapidly evolving field, and the nature of cyber threats is constantly changing. This makes it essential for companies to regularly audit their security controls and update them as necessary to keep them aligned with the latest cyber threats.
By regularly auditing your information security strategy and updating your security policies and controls, you can ensure your company does not fall victim to outdated tools and practices.
6. Incident response plan
Companies tend to focus most of their information security strategy on preventing security breaches. But there are times when prevention is not enough, and responding to a security incident becomes the primary concern.
Your information security strategy should outline the exact steps your company will take in case of a security breach, including procedures for containing the incident, notifying stakeholders, conducting forensic analysis, and recovering affected systems.
7. Disaster recovery planning
Once you’ve contained a security breach, how your company recovers from the incident will play a major role in determining how costly its impact is.
Your company’s information security strategy should include a disaster recovery plan that details the steps to take following a data breach or other security incident, including vital areas of concern such as data recovery, stakeholder/customer communication, and forensic analysis for understanding the cause and scope of the incident.
8. Compliance
You should design your company’s information security strategy to ensure compliance with any legal or regulatory requirements related to data security. This allows you to maintain a strong security posture while also ensuring you remain compliant and avoid the fees and reputational damage that can come from non-compliance.
How Digital Element helps with information security
At Digital Element, we’re committed to helping companies strengthen their information security and prevent costly incidents.
Using patented technology along with over 20 proprietary methods to gain context into IP addresses, Digital Element provides real-time IP intelligence data that brings context and transparency to your company’s information security strategy, helping you identify threats and pinpoint the origins of security breaches.
Digital Element also partners with companies that provide device-derived data from SDKs and apps, enabling even more transparency into your web traffic.
When it comes to empowering better decision-making and faster threat detection, we can’t overstate the value of IP data.
To start leveraging IP intelligence data to bolster your company’s security, learn more about the insights Digital Element has to offer.
Information security use cases
IP intelligence data has several key use cases for strengthening information security. Some of the top use cases for the IP data provided by Digital Element include:
Web Application Firewall (WAF)
A web application firewall (WAF) serves as a gate to keep out suspicious traffic that could pose a security risk. If you don’t know which traffic qualifies as being suspicious, though, the value of this technology is limited.
By using IP data to inform their WAF, companies can effectively identify, process, and potentially block traffic originating from specific areas known for fraudulent activity (for example, traffic originating from countries such as Russia that do not restrict hacking of foreign computer systems).
Once traffic has been flagged based on its origin, companies can then process it according to a set of internal rules, such as invoking multi-factor authentication steps.
VPN usage
VPN usage is on the rise, with the VPN market growing to $31 billion in 2021. This increased usage of VPNs presents a worrying trend for cybersecurity professionals, making it increasingly difficult to analyze web traffic and identify its origin.
Thankfully, an IP intelligence solution such as Digital Element identifies VPN traffic and provides rich insights security professionals can use to detect potential criminal activity, including connection type, log-in location, and domain name.
This goes a long way toward helping companies prevent attacks, such as credential stuffing, that stem from VPN proxies.
IoT devices
IoT devices offer the potential to change the business world as we know it and are already well on their way to doing so. However, a world where everything is connected to the internet (and thus poses a potential security vulnerability) is concerning for many security professionals.
As the prevalence of IoT devices continues to grow, shoring up their vulnerabilities via IP-based information security will be a key cybersecurity objective.
Harness the power of information security with Digital Element
Strong information security is like your company’s armor, ensuring a single cyber attack doesn’t bring the whole operation to a halt. If you want to strengthen your company’s information security and create a comprehensive security strategy, leveraging the power of IP-based data is one of the best steps you can take.
With Digital Element, companies automatically and comprehensively analyze their web traffic to identify and address potential threats before a security incident occurs.
Try Digital Element today and harness the power of IP-based information security.