Account takeover (ATO) refers to the unauthorized access and control of user accounts by malicious actors.
Such breaches pose significant risks to individuals, organizations, and their sensitive data. These breaches lead to financial losses, reputational damage, and privacy violation. Given the evolving sophistication of cyber threats, traditional security measures alone may not suffice to detect and prevent ATO incidents effectively.
As cyber threats become more sophisticated, security measures need effective rules in place to outmaneuver the bad actor without causing user friction. Leveraging advanced tools that incorporate contextual data, especially IP address data, becomes imperative in leveling-up account security measures and thwarting nefarious activity.
The Growing Threat of Account Takeover (ATO)
- In October 2023, three major online services had a flawed implementation of the Open Authorization (OAuth) standard that left millions of users vulnerable for account takeovers on dozens of websites. For users, account takeovers could create life-changing devastation such as credential theft and financial fraud.
- With the rise of AI, bad actors have more tools at their fingertips to take over a user’s account. As AI technology progresses, it can create a convincing mimicry of a person’s voice, photo, and even their writing style. These AI “deep fakes” could lead to higher rates of 401(K) account takeover fraud, according to the National Association of Plan Advisors.
- In September 2022, TechRepublic shared a report citing SEON data that almost 25% of people in the US had been victims of ATOs and the average value of financial losses was $12,000.
The Critical Role of IP Intelligence in ATO Mitigation
- Contextual Understanding
IP address intelligence data offers crucial contextual understanding by providing insights into the geographical origins of login attempts.
This context enables security teams to differentiate between legitimate users and potential threats, facilitating more accurate detection and mitigation of ATO incidents. - Real-Time Monitoring
Platform providers that incorporate IP address intelligence as a contextual dataset enable real-time monitoring of login activities, allowing security teams to promptly identify suspicious behavior indicative of ATO attempts.
Continuous analysis of IP addresses associated with login activities alerts security teams to anomalies so that they can address them with a curated list of customer-specific traffic trends, minimizing risk of successful ATO attempts. - Enhanced Threat Detection
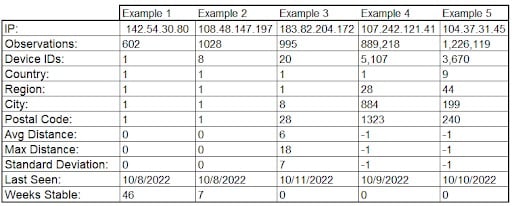
IP address intelligence data enhances threat detection capabilities by enabling the indicators of compromise (IOCs) associated with ATO attacks. For example, monitoring unusual sign-in attempts—people’s habits are predictable—they usually sign in from the same locations and times during the week.
Security professionals can effectively detect compromised accounts by odd sign-in times and from unusual geographies, such as a country where an organization doesn’t have an office or do business.
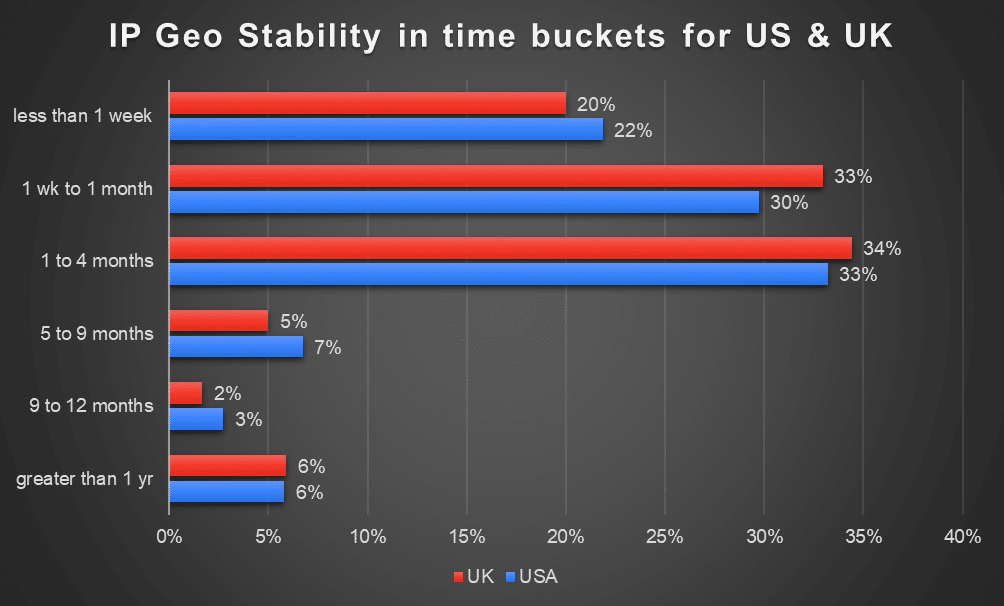
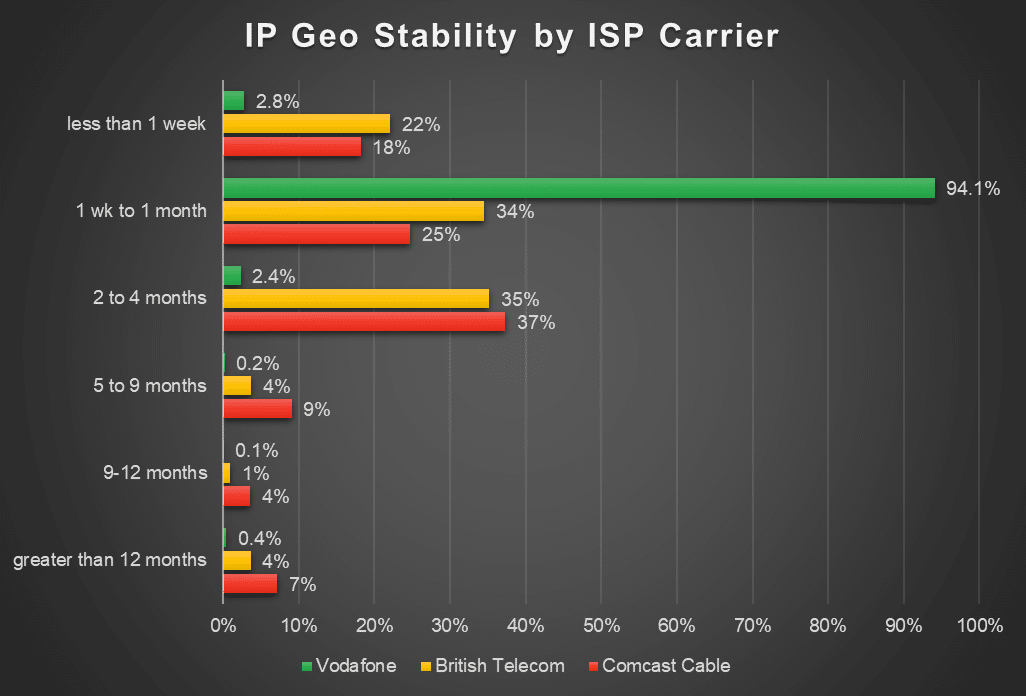
IP address characteristics also allow for the detection of common ways attackers obfuscate their activities to evade detection, such as the use of VPNs or proxys, botnets, high-risk IP addresses, and IP address location instability. Organizations that integrate IP address contextual data into threat detection algorithms can bolster their defenses against ATO attempts and mitigate risks effectively. - Adaptive Security Measures
Leveraging IP address Intelligence data allows for the implementation of adaptive security measures that respond dynamically to emerging threats. Security systems that equip their threat intelligence feeds with continuous IP address contextual data can adapt their defenses in real-time, thereby staying ahead of evolving ATO tactics and techniques.
This adaptive approach enhances the resilience of account security measures and minimizes the likelihood of successful ATO incidents. - Comprehensive Risk Assessment
Integrating IP address contextual data into a risk assessment framework enables organizations to conduct more comprehensive evaluations of ATO risks.
When organizations have insights into factors such as VPN usage, botnet activity, and IP address location stability, they can assign risk scores to login attempts based on their likelihood of being associated with ATO incidents.
This contextual data enables security teams to prioritize response efforts and allocate resources effectively, thereby enhancing overall account security risk assessment.
Partnering with Digital Element for Superior ATO Defense
Digital Element, the authoritative source of IP intelligence data, offers insights that will enhance your organization’s security measures to detect and mitigate account takeover incidents through valuable contextual information associated with IP addresses.
Digital Element revolutionizes fraud detection with our IP address intelligence, offering sophisticated geographic-based insights.
By analyzing sign-in locations, we empower security teams to identify potential fraud through the lens of geographic origin with precision. Additionally, our comprehensive insights into VPN and proxy IP usage equip cybersecurity professionals with crucial contextual data.
This information is pivotal for uncovering and thwarting malicious actors’ efforts to disguise their fraudulent activities. We’re committed to collaborating closely with your data science and development teams, tailoring our best practices to meet your specific Account Takeover (ATO) mitigation requirements.
Interested in enhancing your security measures? Reach out to us to learn more and to have a free assessment specific to your ATO mitigation needs.