A Five-Part Blog Series to Bust the Myths Surrounding VPN Intelligence Data
No trend deserves the corporate security team’s attention more than the explosion of VPN usage, as well as the influx of VPN providers to the market.
The numbers speak for themselves:
- By 2027, the total VPN market may reach $92.6 billion.
- Consumers will contribute to the growth; per IDC, the market for consumer VPNs will double in size, reaching $834 million by 2024.
Countless people will attempt to access corporate systems and websites via a VPN service, forcing security teams to make decisions as to which are legitimate, which are suspect, and which are likely to have nefarious intentions.
In our first blog post of the series, we dispelled the myth that all VPN-driven data is the same. In this post we take on the myth that VPN breadth doesn’t matter.
Myth #2: VPN breadth doesn’t matter. Once you know the entrance IP addresses you have the VPN covered.
Fact: Google “VPN providers” and you’ll see plenty of Top 10 or Top 25 lists, few of which contain the exact same providers. How many VPN services are there exactly? It’s a difficult question to answer, but it’s probably somewhere in the thousands. With that many providers, breadth absolutely matters!
Let’s start with some basics. Not all VPN services are the same. Broadly speaking, there are four main types:
1. Commercial VPN aka Personal VPN
This is a service that’s geared to individual or personal use rather than business use. Personal VPNs are used to protect a home or office computers and devices from external attacks. They’re also used to circumvent geography-based restrictions to content. These can be used on mobile devices, laptops, and home routers.
2. Corporate VPN aka Remote Access
This is a service that allows employees who work remotely to access and use their employers’ corporate data, systems and applications. All traffic between the user and the corporate network is encrypted.
3. Private Relay
This is designed to enable privacy for an individual without allowing them to circumvent geography-based restrictions. The goal of these types of VPNs is to encrypt network traffic to prevent data snooping.
4. Site-to-Site VPN
This is a connection between two or more networks, such as a network within a corporate HQ and one in a local branch office.
Complicating matters further, VPN infrastructure can be quite broad with numerous entry and exit points that change frequently. For instance, a commercial VPN service allows a user to enter the VPN via a US-based IP address and exit it via an IP address that’s located in another country. This allows the user to bypass any geo-restriction policies — an action that you will miss if you have just the US-based point of entry IP address.
Keep in mind that there are many free and low-cost commercial VPN services on the market that offer simple interfaces that allow users to change the location of their IP addresses quickly and easily. In fact, many services offer this functionality as a key selling point.
This means that an employee can also use a personal VPN service from within your corporate campus to circumvent your internal company policies, such as one that bans streaming videos while in the office. Worse, a VPN can be used to exfiltrate internal data outside of the network — an event that security tools can’t always detect.
The bottom line: One IP data point — either the entrance or exit point — is like one hand clapping.
The Digital Element Difference: We are an IP address intelligence data provider that tracks both entrance and exit points of your traffic, which means we are the only company that can eliminate these blindspots for you.
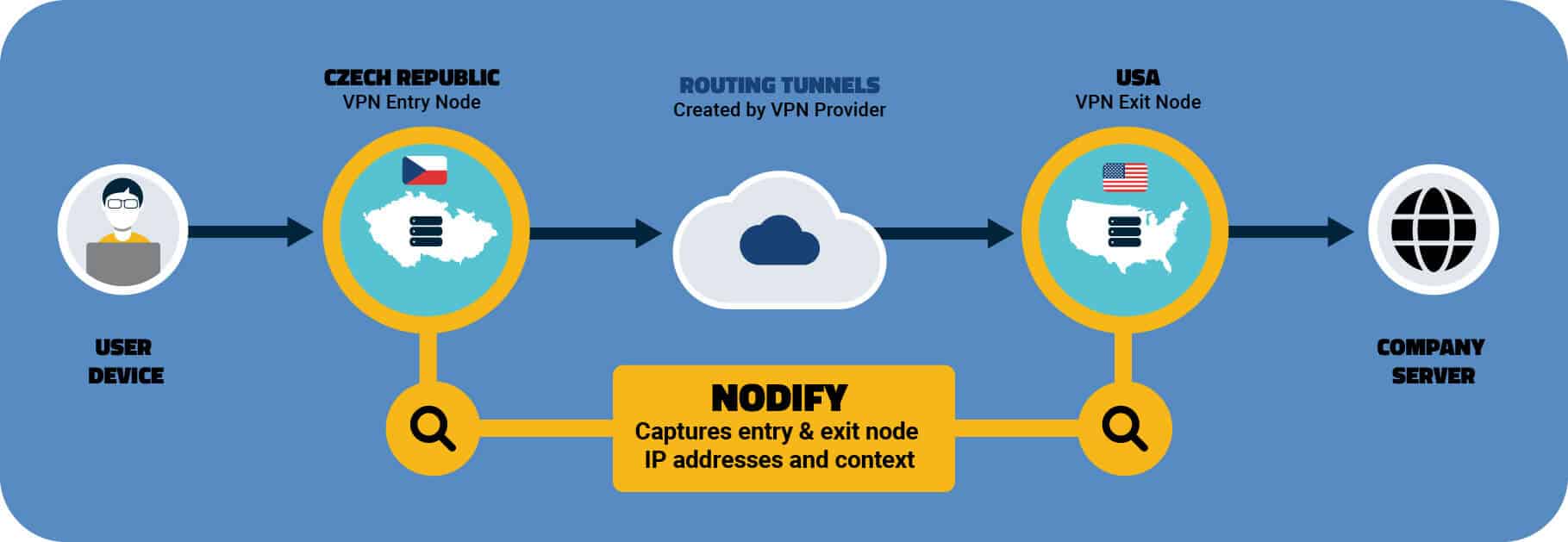
Our breadth of data provides the context you need to protect your corporate network by establishing and implementing best practices about VPN traffic.
Next up: The common myth that covering the top 10 VPN sites provides sufficient protection. We look forward to giving you the whole story on this.
