The Strategic Challenge of Residential Proxies
Residential proxies have become one of the most complex and misunderstood threats in today’s digital ecosystem. Unlike data center proxies, which are relatively easy to detect and often flagged automatically, residential proxies are harder to spot because they route traffic through real consumer devices—like smartphones, laptops, and home routers.
These IP addresses appear legitimate because they are. In many cases, users unknowingly contribute their devices to proxy networks by installing questionable apps, free VPNs, or “free WiFi” services that covertly turn their devices into proxy nodes.
Used for both legitimate and illegitimate purposes, residential proxies sit in a gray area. They can be used for market research, ad verification, and competitive intelligence. But they are also a favored tool for fraudsters seeking to evade detection, bypass security protocols, and appear as “normal” users while conducting malicious activity.
What makes residential proxies uniquely problematic is that they aren’t inherently bad—and that’s exactly what makes them dangerous. Businesses can no longer afford to view them as a binary issue. Instead, organizations need a nuanced, data-driven strategy to identify, understand, and manage residential proxy traffic in a way that balances risk mitigation with user experience.
Understanding Residential Proxy Infrastructure
To navigate the challenges posed by residential proxies, it’s important to understand how they work and why they’re so hard to detect.
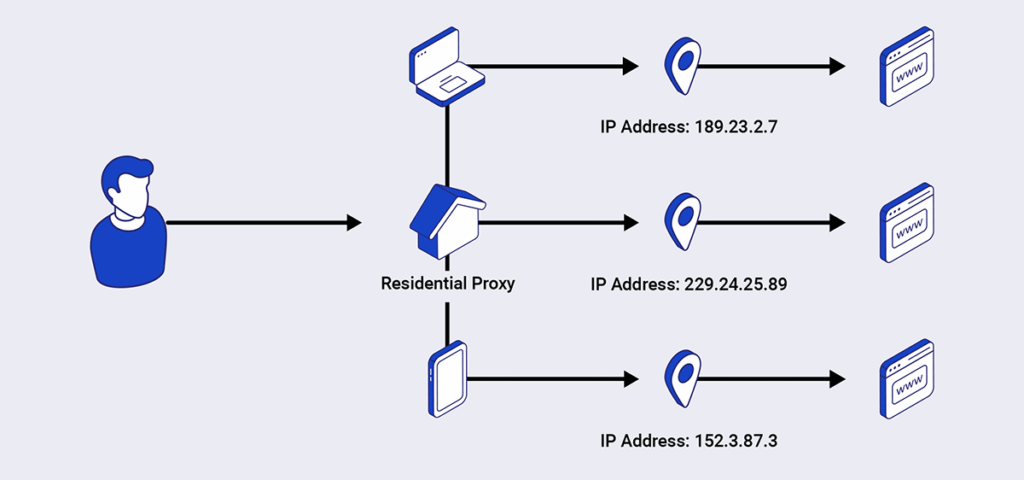
Residential proxies route internet traffic through actual devices—smartphones, laptops, and home routers—connected to legitimate ISPs. These devices are often enlisted via peer-to-peer applications, or worse, through malware infections. This makes the traffic appear organic, masking malicious intent behind what looks like genuine user activity.
Unlike commercial proxy networks or datacenter IPs, which originate from known providers and hosting environments, residential proxies are distributed, dynamic, and nearly indistinguishable from real consumer traffic. This makes them particularly effective for evading traditional detection methods.
They are commonly used in:
- Ad Fraud, where bad actors spoof user behavior to inflate engagement metrics.
- Account Takeovers, where fraudsters test stolen credentials while masking their origin.
- Geo-Restriction Evasion, allowing users—or bots—to access content or services meant for specific regions.
Industries impacted by this phenomenon range widely—from e-commerce platforms combating bot-driven cart sniping and checkout fraud, to streaming services enforcing geographic licensing terms, to adtech companies combatting ad fraud, to fintech firms defending against synthetic identity attacks.
According to industry reports, the use of residential proxies in fraud-related activity has grown significantly over the past five years, fueled by easy access to “residential IP pools” for rent and the rising sophistication of proxy-as-a-service platforms.
Why are residential proxies becoming more popular?
- They’re hard to detect using traditional IP lookups.
- They rotate frequently, simulating natural user behavior.
- They work—for both good and bad actors.
The Core Challenge: You Can’t Just Block Them All
The instinctive response might be to block all residential proxies—but that approach backfires quickly. Legitimate users often share the same infrastructure as attackers. Blocking residential proxy IPs might also mean blocking your own customers—especially in industries like streaming, gaming or ecommerce. The result? False positives, lost revenue, and damaged trust.
Instead of treating all residential proxy traffic as malicious, businesses need to ask smarter questions:
- What percentage of our traffic is coming from residential proxies?
- Are these proxies being used for abuse—or innocently?
- Do we have the right data to confidently decide what to block?
If you don’t know what you’re dealing with, you can’t make informed decisions. That’s where most organizations fall short.
The Strategic Blind Spot
Despite their growing prevalence, many organizations have yet to define a clear policy around residential proxy traffic. This oversight creates a critical blind spot—one that can expose companies to fraud, abuse, and costly customer friction.
Part of the problem is overreliance on basic IP geolocation tools, which provide surface-level insights like country, region, and ISP but lack the additional context needed to assess risk. Businesses may know where traffic is coming from, but not what it represents.
Is the IP address tied to a rotating proxy? A compromised device? A VPN? Without this level of granularity, companies are forced to guess, which often leads to one of two poor outcomes: either they block legitimate users or let bad actors through.
To move forward, businesses must start by understanding more about their traffic. What percentage of it is coming from residential proxies? How does it vary by region or user behavior? What patterns are emerging over time? The answers to these questions are foundational to developing a smarter, more resilient response strategy.
Residential Proxies Across Industries: A Growing Threat
Across industries, residential proxy usage is becoming harder to ignore—and inaction is no longer a viable strategy. As businesses grow more reliant on digital channels, the gray area surrounding residential proxy traffic is leading to real-world consequences.
Consider the following scenarios:
- Streaming & Digital Rights Management (DRM): Streaming services must enforce geographic licensing agreements—but residential proxies make that increasingly difficult. Unlike VPNs, which are now widely blocked, residential proxies often go undetected. A user in a restricted territory may appear to be streaming from a valid U.S. location, violating license terms and threatening compliance.
Conversely, overcorrecting can mean blocking legitimate subscribers, especially if they share an IP range with a flagged residential proxy pool. Either way, the business loses. - E-Commerce & Ticketing Abuse: Online retailers and ticketing platforms have become prime targets for residential proxy exploitation. Scalpers, for instance, use rotating residential proxy networks to appear as thousands of unique buyers—evading purchase limits and CAPTCHAs to hoard high-demand items like concert tickets. These attacks often occur at lightning speed and from IPs that look indistinguishable from real consumers.
Without advanced detection, businesses can’t distinguish between a loyal shopper and an opportunistic bot. The result: frustrated customers, inventory abuse, and reputational damage. - Fraud Detection & Risk Scoring: In sectors like fintech and cybersecurity, fraud detection systems rely heavily on IP reputation and behavioral scoring. Residential proxies disrupt those systems. They allow fraudsters to bypass location-based risk filters, manipulate identity signals, and impersonate real users.
Without deeper insight into proxy usage, scoring models break down—leading to false positives that inconvenience users, or false negatives that let attackers in. The stakes are high: reputational damage, regulatory exposure, and direct financial loss.
These real-world challenges point to a central truth: traditional IP insights aren’t enough. Residential proxies undermine surface-level trust signals and demand deeper, contextual intelligence to be managed effectively. Businesses must evolve from reactive blocks to proactive strategies grounded in a full understanding of their traffic.
What to Do with Residential Proxy Data
Detection alone is not enough. Organizations that recognize residential proxy traffic must also decide how to respond—and that response must be aligned with business objectives and risk tolerance.
Key strategies include:
- Adapting fraud scoring: Adjust models based on proxy type and behavioral signals. Residential proxies may not warrant an automatic block but could require increased scrutiny.
- Enabling step-up authentication: For transactions or login attempts from flagged IPs, introduce additional verification methods—like SMS codes or biometric prompts—to ensure legitimacy without blocking outright.
- Personalizing content delivery: Treat suspicious sessions differently. Limit access to high-value actions (like checkout or media playback) until more signals are available.
- Logging and pattern detection: Flag repeated behavior from residential proxy pools for long-term analysis. Understanding how often these IPs are seen, noting the proxy provider, and in what context can lead to more refined segmentation and response strategies.
Ultimately, companies must define a clear policy: not just if they’ll respond to residential proxy traffic—but how.
How Digital Element Fills the Gap
To act confidently in this gray area, businesses need more than just IP location—they need IP context. Digital Element’s IP Characteristics (IPC) provides the critical observational insights required to help assess the role an IP address plays in digital interactions.
Rather than directly flagging IP addresses as proxies or VPNs, IPC offers device derived signals for a given IP address—such as device counts and geographic stability—that help organizations make informed, evidence-based decisions. When combined with classification solutions like Nodify, which explicitly categorize IP addresses as residential proxies, VPNs, or hosting infrastructure, these insights enable smarter, more precise outcomes.
With IPC, companies can:
- Assess behavioral patterns associated with IP addresses to help differentiate between typical residential activity and traffic that may be linked to data centers, hosting environments, or proxy services.
- Corroborate VPN or hosting infrastructure usage by analyzing device behavior and network stability, providing supporting evidence that an IP address may be part of a VPN or proxy network.
- Understand the underlying risk posture of each IP address by evaluating persistence at specific locations, volume of unique devices observed, and frequency of geographic changes.
- Enhance fraud and risk models by integrating verified behavioral insights, improving accuracy without introducing unnecessary user friction.
By leveraging IPC alongside classification tools like Nodify, businesses can move beyond binary block-or-allow decisions—enabling proportional, informed responses that protect revenue while preserving customer trust.
Don’t Let the Gray Area Stay Gray
Residential proxies are here to stay. They are a tool—neutral in theory, but powerful in practice—and increasingly exploited by those looking to bypass rules, manipulate systems, or obscure intent.
For organizations that care about security, compliance, and customer trust, doing nothing is no longer an option.
Digital Element’s IPC and Nodify equips businesses with the visibility they need to turn ambiguity into action. With nuanced insights and contextual awareness, companies can respond proportionally, intelligently, and confidently.
Because in an environment where gray areas abound, clarity is your greatest competitive edge.
Ready to Take Control of Residential Proxy Traffic?
Don’t settle for guesswork. Gain the visibility and intelligence you need to protect your business, reduce fraud, and make confident, data-driven decisions.
Chat with one of our experts to learn how IPC and Nodify can help you manage residential proxy traffic with precision and confidence.